Quantum Cyber Security Services & Solutions in Belgium
Price and ROI of Private Cloud
According to a study that surveyed 150 IT decision-makers, private cloud costs are lower than equivalent public cloud server pricing, especially if you rent long term. A private cloud also saves a lot of money on personnel and compliance costs since this ESG investment will drastically lower your carbon footprint
Crypto Agility
To ensure survival and withstand uncertain cryptographic times our solutions are crypto-agile, that means we can update the algorithms quickly when a standard might be deemed unsafe or new standards are released. This would be a lot harder and takes more valuable time in a public cloud setting
Time Storage
Compliance
A private cloud is the best option towards compliance because it offers the highest degrees of privacy. Thanks to quantum authentication you can also ensure access is only granted to the people and devices that truly need it. (complete built-in zero-trust model). This innovative technology also considers the environment and our planet
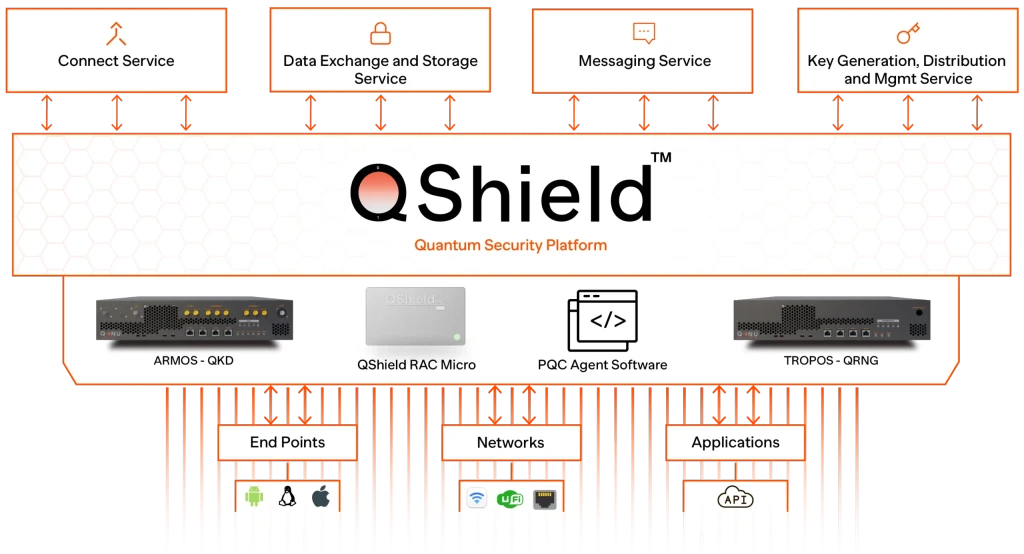
Next generation platforms secured by our cyber security technologies
Secure your environment from malicious post quantum and generative AI cyber attacks, QS dome is a complete end to end cloud or data-centre solution for the most complex data and infrastructure requirements.
Quantum Computing
Quantum dome supports Quantum Machine Learning, Quantum Sensing and Quantum Optimisation platforms.
Quantum Key Distribution
Supports Quantum Key Distribution for enterprise networks, and supports QKD hardware and software.
Supports PQC
Supports Post Quantum Cryptography for both
cloud and mobile endpoint integrations.
OT/IOT Security
Supports IOT and OT endpoints connected to the cloud or the physical network.
Physical Security
Supports surveillance camera's, Domotica, Biometrics, Fencing, Alarms, Locks and more.
QRNG
Supports and integrates Quantum Random Number Generators.
A New Level Of Cryptographic Protection
This solution addresses a critical gap in the cybersecurity landscape by implementing the following two key enhancements:
Replacing the inherently weak internal key expansion function ('key schedule') with a cryptographically robust pseudo-random generator.
Doubling the number of transformation rounds to at least 2n, or at least twice the count required to withstand the most advanced cryptanalytic attacks against AES ciphers.
By incorporating these measures, eAES® provides a provably secure and effective solution for ensuring the long-term security of AES ciphers. This plug-and-play solution requires no additional hardware or software investments, safeguarding existing technological investments while significantly mitigating many of the most severe known attacks against the AES family of cryptosystems.
Software Libraries
API Security - Secure File Server - Secure boot loader and installer - OS entropy hardener - Digital QKD
Mobile SIM and e-SIM
PQC protection of SIM and/or eSIM cards in mobile devices, vehicles or endpoints.
Harddisk and USB
PQC protection of USB sticks and external hard drives/storage drives and protects your data at rest/
Quantum Safe VPN
-Secure your in-transit data with truly unpredictable keys, and multiplicity in authentication is highly scalable, providing mnimal latency and is Work-From-Home Ready
Entropy as a Service (EaaS)
API runtime environment provides a seamless integration with multiple deployment options. Host the entire solution in your data center or client location.
Quantum Safe Messenger
Provided end-to-end encrypted group chats with forwarding security, user verification, quantum-secured HD-Quality for Voice and Video
and Secure File Transfers

Elevate your security posture by transitioning to the new Quantum Reality. Our services help you correctly implement Quantum-Safe Security, Quantum Key Distribution, Quantum Cryptography, and AI.
With our extensive experience in IT, security, and development, we provide tailor-made advice and solutions for your company's networks and facilities, using a Crypto-Agile and Hybrid approach to ensure resilience in times of cryptographic uncertainty.
Our expertise spans Quantum Machine Learning, AI, and communication implementations, and we offer our services worldwide, including Quantum Governance and Risk Assessments, Physical Security Assessments, and Penetration Testing.

Security Assessments
The BLACKHILLS Quantum Team Holds Multiple World-Renowned Cybersecurity Certifications from the three leading certification bodoes, ISACA, CompTIA and ICS2

CompTIA Security+ ce Certification
CompTIA Security+ professionals know how to identify and address potential threats, attacks and vulnerabilities and they have established techniques in risk management, risk mitigation, threat management and intrusion detection

Certified in Cybersecurity (CC)
The CC proves to organizations that certified team members understand fundamental security principles, operations, network security, access controls and that they have the skills to meet and exceed performance standards

CISA: Certified InfoSystems Auditor
The CISA certification from ISACA is world-renowned as the standard of achievement for those who audit, control, monitor and assess an organisation’s information technology and business systems.
Our Partners
ARMOS - Quantum Key Distribution (QKD)
The ultimate shield for your data
QNu’s Armos QKD protects critical infrastructure unconditionally, providing quantum resilience to ensure data in transit is safe at all times.
Root of trust giving the perfect random numbers
QNu' Tropos (QRNG) does not rely on mathematical algorithms; it generates random numbers from a quantum source, making it suitable for all applications.
QShield™
Secure Messaging with the World's First Quantum Secure Messenger. QNu Labs bring to you the world's first quantum secure messenger, QShield™. Equipped with quantum-derived primitives that provide end-to-end security for all your digital correspondence.
QRCrypto
QRCrypto’s patented technology corrects the Achilles heel of cybersecurity by strengthening the key schedule of FIPS AES with a cryptographically strong pseudo-random generator, thereby increasing its key size.
By doing so, eAES® acts as a working and provably secure solution to the question of the AES cipher’s sustainable long-term security.
Most important, eAES® is a plug & play solution; there is no need to purchase new hardware or other software, preserving the large investments that have been made in this technology, while strongly mitigating many of the most serious known attacks against the AES family of cryptosystems.
From space infrastructure to blockchain to quantum light solutions and more, QRC is protecting the world's most sensitive information from today’s hackers, leaks, and the inevitability of quantum computers.

Quintessence Labs
QuintessenceLabs is at the forefront of quantum cybersecurity, providing the strongest data protection to keep your information safe against today’s and tomorrow’s threats.
Our capabilities extend from quantum key generation and crypto-agile key management through to quantum key distribution, helping you build a quantum-safe future for your organization

Trusted Security Foundation
Enterprise Key and Policy Manager.
Centralized and vendor-neutral encryption key management solution. Designed to easily address the toughest challenges in key management. Crypto agile adaptable to quantum resistant algorithms
qOptica100 Quantum Key Distribution
Point-to-point protocol that uses specialized hardware to share secret keys over an optical link
Secrecy of the keys is guaranteed by the laws of quantum physics
Offers CV-QKD technology with built-in advantages in terms of cost, form factor, and performance
Stream™ Quantum Random Number Generator (QRNG)
Derived from a quantum source
Generates perfectly unpredictable true random numbers
Delivered at the speeds needed for commercial applications (up to 1Gbps)
Provides high quality entropy for stronger encryption keys
Facial Recognition Software
Verify anyone from anywhere in under one secondFacia empowers the world's fastest and most accurate face recognition solution with instant liveness detection. Our solutions include face search, face matching, age verification, liveness detection and iris recognition.
AI Verification Software
World's largest and most accurate primary data source for companies verification.
UK Channel Partner
The innovation partner for UK Justice & Legal.
We make digital transformation procurement and delivery safe and easy, to maximise your return on innovation investment.
Post-Quantum Cryptography for Quantum-Secure Asymmetric Encryption
Post-Quantum Cryptography for Quantum-Secure Asymmetric Encryption
QEEP
QEEP™ provides enhanced quantum-secure symmetric encryption functionality. Powered by Quantropi’s Quantum Permutation Pad (QPP) technology, which achieves Shannon Perfect Secrecy, QEEP™ extends the symmetric encryption key length well beyond the current 256-bit limit.

BELGIUM
Heilig Hartplein
Hasselt, Belgium
info@blackhillsquantum.com
EU +32(0)456 32 80 09
USA
8, The Green, Dover,
Delaware
info@blackhillsquantum.com
US +1 (302) 217-6933
Mail: info@blackhillsquantum.com
VAT:BE1008.029.146.
Duns: 37-303-0074
EIN: 320744563
Lower your Carbon Footprint with
ESG from Blackhills Quantum
Privacy Policy
Website By WizzWang Deep Tech
Blackhills Quantum Computing and marketing Privacy Policy
Introduction
This Privacy Policy outlines Blackhills Quantum practices with respect to information collected from users who access our website at www.blackhillsquantum.com or otherwise share personal information with us (collectively: " Users ").
Grounds for data collection
Processing of your personal information (meaning, any information which may potentially allow your identification with reasonable means; hereinafter " Personal Information ") is necessary for the performance of our contractual obligations towards you and providing you with our services, to protect our legitimate interests and for compliance with legal and financial regulatory obligations to which we are subject.When you use the Site, you consent to the collection, storage, use, disclosure and other uses of your Personal Information as described in this Privacy Policy.We encourage our Users to carefully read the Privacy Policy and use it to make informed decisions.
What information we collect?
We collect two types of data and information from Users.
The first type of information is un-identified and non-identifiable information pertaining to a User(s), which may be made available or gathered via your use of the Site (“ Non-personal Information ”). We are not aware of the identity of a User from which the Non-personal Information was collected. Non-personal Information which is being collected may include your aggregated usage information and technical information transmitted by your device, including certain software and hardware information (e.g. the type of browser and operating system your device uses, language preference, access time, etc.) in order to enhance the functionality of our Site. We may also collect information on your activity on the Site (e.g. pages viewed, online browsing, clicks, actions, etc.).
The second type of information Personal Information which is individually identifiable information, namely information that identifies an individual or may with reasonable effort identify an individual. Such information includes:Device Information: We collect Personal Information from your device. Such information includes geolocation data, IP address, unique identifiers (e.g. MAC address and UUID) and other information which relates to your activity through the Site.
Registration information: When you register to our Site you will be asked to provide us certain details such as: full name; e-mail or physical address, and other information.
How do we receive information about you?
We receive your Personal Information from various sources:When you voluntarily provide us your personal details in order to register on our Site;When you use or access our Site in connection with your use of our services;From third party providers, services and public registers (for example, traffic analytics vendors).
What information we collect?
We do not rent, sell, or share Users’ information with third parties except as described in this Privacy Policy.
We may use the information for the following:Communicating with you – sending you notices regarding our services, providing you with technical information and responding to any customer service issue you may have;To communicate with you and to keep you informed of our latest updates and services;To serve you advertisements when you use our Site (see more under "Advertisements"); To market our websites and products (see more under "Marketing"); Conducting statistical and analytical purposes, intended to improve the Site.…
In addition to the different uses listed above, we may transfer or disclose Personal Information to our subsidiaries, affiliated companies and subcontractors.
In addition to the purposes listed in this Privacy Policy, we may share Personal Information with our trusted third party providers, who may be located in different jurisdictions across the world, for any of the following purposes: Hosting and operating our Site;
Providing you with our services, including providing a personalized display of our Site;Storing and processing such information on our behalf; Serving you with advertisements and assist us in evaluating the success of our advertising campaigns and help us retarget any of our users;Providing you with marketing offers and promotional materials related to our Site and services; Performing research, technical diagnostics or analytics;We may also disclose information if we have good faith to believe that disclosure of such information is helpful or reasonably necessary to: (i) comply with any applicable law, regulation, legal process or governmental request; (ii) enforce our policies (including our Agreement), including investigations of potential violations thereof; (iii) investigate, detect, prevent, or take action regarding illegal activities or other wrongdoing, suspected fraud or security issues; (iv) to establish or exercise our rights to defend against legal claims; (v) prevent harm to the rights, property or safety of us, our users, yourself or any third party; or (vi) for the purpose of collaborating with law enforcement agencies and/or in case we find it necessary in order to enforce intellectual property or other legal rights.
User Rights
You may request to: Receive confirmation as to whether or not personal information concerning you is being processed, and access your stored personal information, together with supplementary information.
Receive a copy of personal information you directly volunteer to us in a structured, commonly used and machine-readable format.
Request rectification of your personal information that is in our control.
Request erasure of your personal information.
Object to the processing of personal information by us.
Request to restrict processing of your personal information by us.
Lodge a complaint with a supervisory authority.
However, please note that these rights are not absolute, and may be subject to our own legitimate interests and regulatory requirements.
If you wish to exercise any of the aforementioned rights, or receive more information, please contact our Data Protection Officer (“DPO”) using the details provided below:info@blackhillsquantum.com.
Retention
We will retain your personal information for as long as necessary to provide our services, and as necessary to comply with our legal obligations, resolve disputes, and enforce our policies. Retention periods will be determined taking into account the type of information that is collected and the purpose for which it is collected, bearing in mind the requirements applicable to the situation and the need to destroy outdated, unused information at the earliest reasonable time. Under applicable regulations, we will keep records containing client personal data, account opening documents, communications and anything else as required by applicable laws and regulations.
We may rectify, replenish or remove incomplete or inaccurate information, at any time and at our own discretion.
Cookies
We and our trusted partners use cookies and other technologies in our related services, including when you visit our Site or access our services.
A "cookie" is a small piece of information that a website assign to your device while you are viewing a website. Cookies are very helpful and can be used for various different purposes. These purposes include allowing you to navigate between pages efficiently, enable automatic activation of certain features, remembering your preferences and making the interaction between you and our Services quicker and easier. Cookies are also used to help ensure that the advertisements you see are relevant to you and your interests and to compile statistical data on your use of our Services.
The Site uses the following types of cookies:
a. 'session cookies' which are stored only temporarily during a browsing session in order to allow normal use of the system and are deleted from your device when the browser is closed;
b. 'persistent cookies ' which are read only by the Site, saved on your computer for a fixed period and are not deleted when the browser is closed. Such cookies are used where we need to know who you are for repeat visits, for example to allow us to store your preferences for the next sign-in;
c. 'third party cookies' which are set by other online services who run content on the page you are viewing, for example by third party analytics companies who monitor and analyze our web access.
Cookies do not contain any information that personally identifies you, but Personal Information that we store about you may be linked, by us, to the information stored in and obtained from cookies. You may remove the cookies by following the instructions of your device preferences; however, if you choose to disable cookies, some features of our Site may not operate properly and your online experience may be limited.
We also use a tool called “Google Analytics” to collect information about your use of the Site. Google Analytics collects information such as how often users access the Site, what pages they visit when they do so, etc. We use the information we get from Google Analytics only to improve our Site and services. Google Analytics collects the IP address assigned to you on the date you visit sites, rather than your name or other identifying information. We do not combine the information collected through the use of Google Analytics with personally identifiable information. Google’s ability to use and share information collected by Google Analytics about your visits to this Site is restricted by the Google Analytics Terms of Use and the Google Privacy Policy.
Third party collection of information
Our policy only addresses the use and disclosure of information we collect from you. To the extent you disclose your information to other parties or sites throughout the internet, different rules may apply to their use or disclosure of the information you disclose to them. Accordingly, we encourage you to read the terms and conditions and privacy policy of each third party that you choose to disclose information to.
This Privacy Policy does not apply to the practices of companies that we do not own or control, or to individuals whom we do not employ or manage, including any of the third parties which we may disclose information as set forth in this Privacy Policy.
How do we safeguard your information?
We take great care in implementing and maintaining the security of the Site and your information. Although we take reasonable steps to safeguard information, we cannot be responsible for the acts of those who gain unauthorized access or abuse our Site, and we make no warranty, express, implied or otherwise, that we will prevent such access.
Transfer of data outside the EEA
Please note that some data recipients may be located outside the EEA. In such cases we will transfer your data only to such countries as approved by the European Commission as providing adequate level of data protection, or enter into legal agreements ensuring an adequate level of data protection.
Advertisements
We may use a third-party advertising technology to serve advertisements when you access the Site. This technology uses your information with regards to your use of the Services to serve advertisements to you (e.g., by placing third-party cookies on your web browser).
You may opt-out of many third-party ad networks, including those operated by members of the Network Advertising Initiative ("NAI") and the Digital Advertising Alliance ("DAA"). For more information about this practice by NAI and DAA members, and your choices regarding having this information used by these companies, including how to opt-out of third-party ad networks operated by NAI and DAA members, please visit their respective websites: http://optout.networkadvertising.org/#!/ and http://optout.aboutads.info/#!/.
Marketing
We may use your Personal Information, such as your name, email address, telephone number, etc. ourselves or by using our third party subcontractors for the purpose of providing you with promotional materials, concerning our services, which we believe may interest you.
Out of respect to your right to privacy we provide you within such marketing materials with means to decline receiving further marketing offers from us. If you unsubscribe we will remove your email address or telephone number from our marketing distribution lists.
Please note that even if you have unsubscribed from receiving marketing emails from us, we may send you other types of important e-mail communications without offering you the opportunity to opt out of receiving them. These may include customer service announcements or administrative notices.
Corporate transaction
We may share information in the event of a corporate transaction (e.g. sale of a substantial part of our business, merger, consolidation or asset sale). In the event of the above, the transferee or acquiring company will assume the rights and obligations as described in this Privacy Policy.
Minors
We understand the importance of protecting children’s privacy, especially in an online environment. The Site is not designed for or directed at children. Under no circumstances shall we allow use of our services by minors without prior consent or authorization by a parent or legal guardian. We do not knowingly collect Personal Information from minors. If a parent or guardian becomes aware that his or her child has provided us with Personal Information without their consent, he or she should contact us at info@blackhillsquantum.com.
Updates or amendments to this Privacy Policy
We reserve the right to periodically amend or revise the Privacy Policy; material changes will be effective immediately upon the display of the revised Privacy policy. The last revision will be reflected in the "Last modified" section. Your continued use of the Platform, following the notification of such amendments on our website, constitutes your acknowledgment and consent of such amendments to the Privacy Policy and your agreement to be bound by the terms of such amendments.
How to contact us
If you have any general questions about the Site or the information we collect about you and how we use it, you can contact us at info@blackhillsquantum.com.
Last Modified 31/7/2023